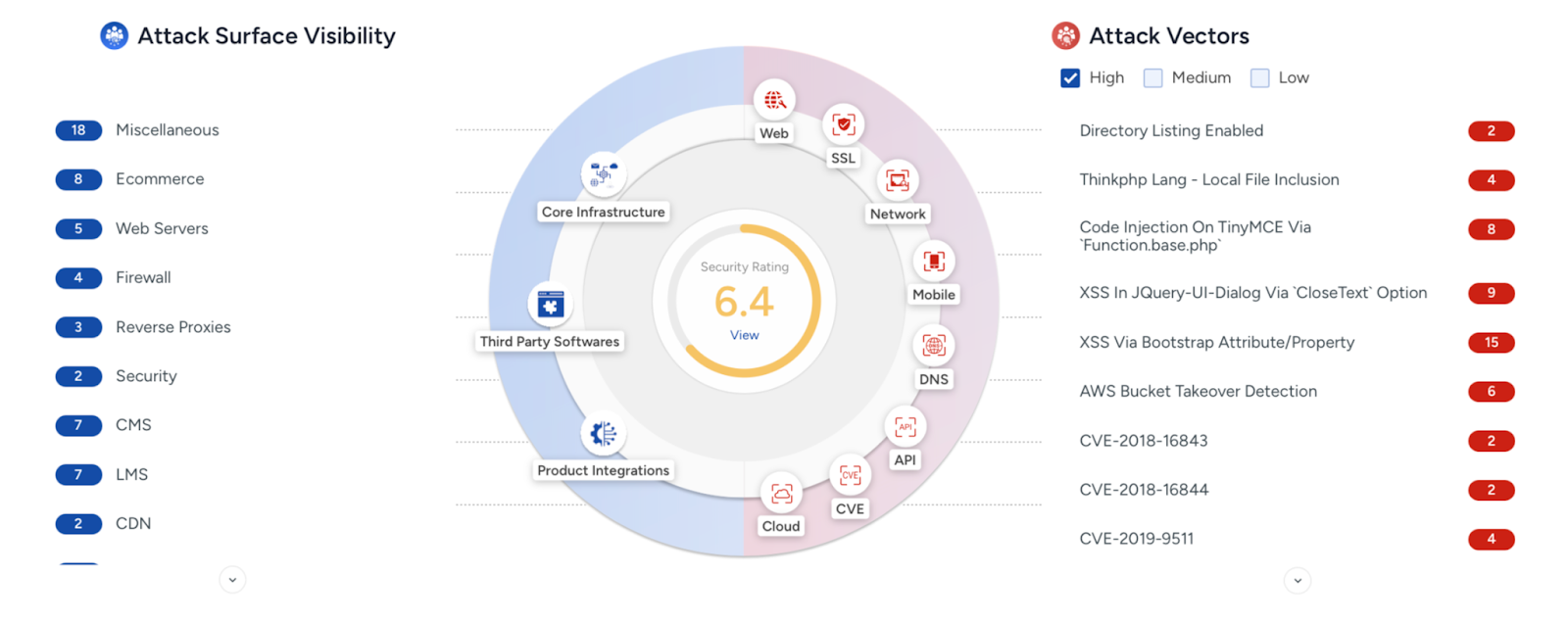
A major data security incident has been uncovered where sensitive information of over 33,000 employees was exposed due to unsecured API endpoints.
CloudSEK’s BeVigil security platform discovered that a prominent technology service provider left critical API endpoints completely unprotected, allowing unrestricted access to confidential employee data without any authentication mechanisms in place.
This concerning issue not only compromised personal and organizational data but also highlighted the growing risks associated with misconfigured APIs in enterprise environments.
Unauthenticated API Endpoints Expose Internal Data
BeVigil’s WebApp scanner detected multiple unauthenticated RESTful API endpoints associated with the tech provider’s internal web application.
These vulnerable endpoints were configured without proper OAuth 2.0 authentication or API key validation, creating a significant security gap in the company’s infrastructure.
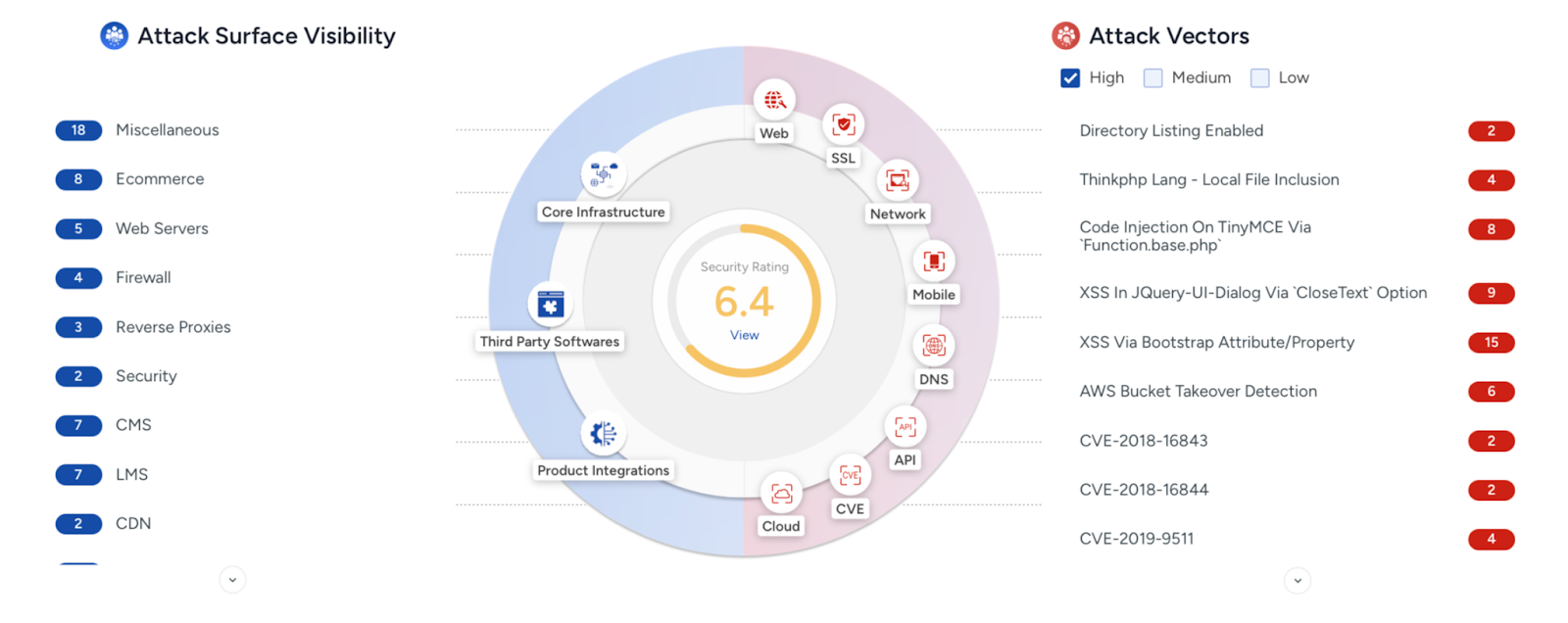
“Any attacker could simply send an HTTP request and extract confidential data without any authentication barriers,” CloudSEK researchers shared with Cyber Security News.
The exposed endpoints followed a predictable URL pattern of https://api.internal.company.com/v1/employees/ making them easily discoverable by automated scanning tools.
The HTTP GET requests to these endpoints returned JSON responses containing:

This misconfiguration violates fundamental API security principles, specifically OWASP API Security Top 10 risk A2:2023 (Broken Authentication).
Exposed Information and Risks
The compromised data included employee personal information (PII), hardware asset details, and internal project structures. Security experts warn that this breach creates multiple cascading security risks:
- Unauthorized data exfiltration potential, allowing threat actors to download and analyze organizational hierarchies and identify key personnel
- Expanded attack surface for cybercriminals, as the exposed API endpoints provided real-time data updates, enabling continuous monitoring of employee activities and infrastructure changes
- Enhanced social engineering vectors, where attackers could craft convincing phishing campaigns by impersonating internal IT teams with legitimate employee information.

Recommended Mitigation Measures
Security professionals recommend immediate implementation of:
- API gateway protection with proper JWT token validation.
- Rate limiting and request throttling to prevent abuse.
- Encryption of all PII data both in transit and at rest.
- Comprehensive API monitoring and logging solutions.
- Credential rotation for all potentially compromised accounts.
This breach serves as a stark reminder that even major technology providers can overlook fundamental security practices.
Organizations must adopt proactive API security postures to prevent similar vulnerabilities, as the consequences of exposed endpoints can lead to data breaches, regulatory penalties, and significant reputational damage.